Application servers are essential components of any modern IT infrastructure. They host mission-critical applications that businesses rely on for their day-to-day operations. As such, it's crucial to ensure that application servers are secure and protected against cyber-attacks. Penetration testing is one effective way to identify vulnerabilities and potential exploits in an application server. In this article, we'll explore what application server penetration testing entails and how it works.
What is Application Server Penetration Testing?
Application server penetration testing is a security testing methodology used to evaluate the security posture of application servers. The process involves simulating attacks against the application server to identify vulnerabilities that attackers could exploit to gain unauthorized access, steal sensitive data or compromise the system. The objective of penetration testing is to identify security flaws before cyber-criminals can find them and exploit them.
The Application Server Penetration Testing Process
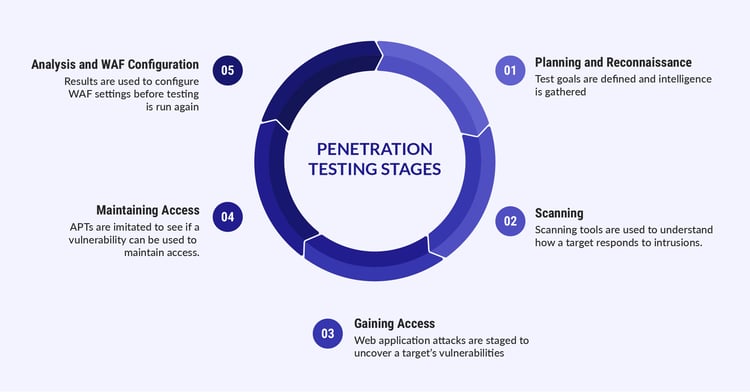
The application server penetration testing process typically follows the following steps:
Application Server Penetration Testing Tools
Application server penetration testing tools can help streamline the testing process and make it more efficient. Here are some of the most popular penetration testing tools for application servers:

Conclusion
Application server penetration testing is a crucial part of any comprehensive security program. By simulating attacks against the application server, businesses can identify vulnerabilities and potential exploits that could be used by cyber-criminals to compromise their systems. With the right tools and testing methodology, businesses can stay ahead of the curve and ensure that their application servers are secure and protected against cyber-attacks.